Location: Room 1300 — Conrad Grebel University College, 140 Westmount Rd. N. · Waterloo, ON N2L 3G6 (bottom floor, in the hallway that connects the main building to the Chapel-Residence building)
Date: Monday, 11 March 2019
Time: 7:00-9:00PM
We’ve talked about Malware and the importance of Keeping Computers Up To Date, and even just about The Things We Should Fear. But what new hazards are unveiled when you connect two or more computers together? When some of those computers aren’t on your own network? When malusers are out there trying to break into your network? When you’re actually inviting everyone into your network by running servers and services? Should you just outsource everything? Or are there tools available for the Non-Profit SysAdmin to help secure your networks?
We’ll talk about the hazards of running a public network, and go over a list of tools and software.
–Marc Paré & Bob Jonkman
Resources
- Firewalls
- The most secure firewall:

- Another secure firewall: pfSense
- The most secure firewall:
- Intrusion Detection Software
- Pen Testing apps
- Claim: The greatest threat in Network Security is NetAdmin or User Error
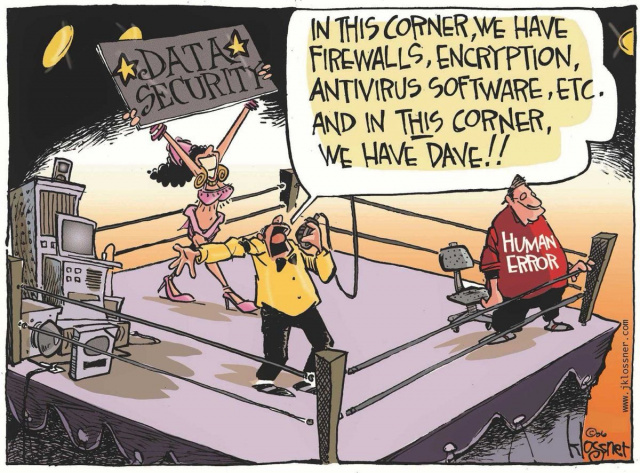
- Another e-mail breach caused by human error:
- Data exfiltration due to user error:
- NetAdmin failed to renew expired domain names:
- Vulnerability not acknowledged by vendor:
- City knew of massive cyber breach days before admitting it | CBC News
-
On Dec.19, the day following Solomon’s exchange with Caissie, the city received notice from CentralSquare Technologies, the Florida company providing the Click2Gov parking server software, that there was no problem with the system. “Resolution: Checked Click2Gov server for evidence of malware/possible breach, no evidence found of breach/malware,” says the statement signed only “Customer Support.”
- Pre-emptive shutdown of mail system to prevent a virus attack that might shut down the mail system.
Meeting Notes
Spoke about resources, war stories
- Proprietary mail systems
- Errors in implementation, makes mail inaccessible, or sends mail when unwanted.
- Corporate culture prevents people from speaking of security flaws
- Bugs in the software
- Errors in procedures
The Cloud
- “If the data was in the cloud it would have been safe”
- What is The Cloud?
- Somebody manages the servers, still subject to human error
- But reduces the human interaction that is needed
- Maybe if everything is run by robots…
- But that’s not the way Nonprofits operate, engaging people to be more involved
- Open Source groups want more interaction, so still room for error
- eg. LibreOffice: Get a professional to manage website? Or keep local group involvement? No to robots
- Robots have programmers too
- One more level of abstraction
- Problems solved?
- Email spoofing, phishing schemes: Joe Jobs, third-party addressbooks breached
- Could contact the apparent sender, but that person may not be involved in the message at all
